WEGnology Security Overview
The WEGnology IoT application enablement platform keeps our customers’ solutions protected by using the highest level of security. WEGnology uses industry-standard encryption mechanisms to fully encrypt all data during transit and while at rest. This article provides a detailed overview of how WEGnology provides a secure environment for its users and applications.
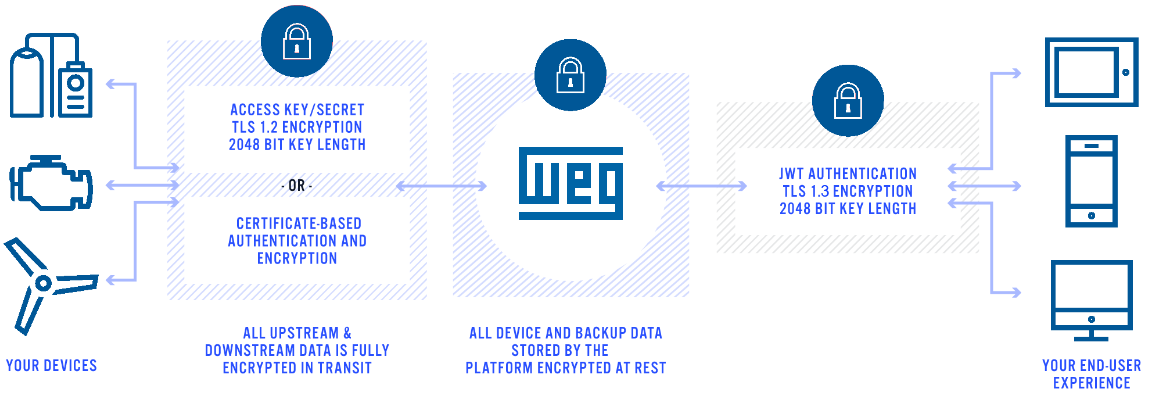
Transport Security
All communication between devices and WEGnology is fully encrypted using Transport Security Layer (TLS) 1.2 or 1.3. TLS is an industry-standard encryption scheme and most commonly used by browsers to encrypt HTTPS data. TLS is widely adopted and available on most devices, languages, and operating systems.
API Security Tokens
API access is controlled by the industry-standard JSON Web Tokens authentication mechanism. Users create remote API access tokens through the account dashboard. The types of resources available to the token can be individually controlled depending on the needs of the specific API client. For example, an application that only needs access to view data can generate a token that just grants access to data. This token is not be able to view, edit, or manage any information about workflows or devices. API access tokens can be revoked at any time.
WEGnology does not store the tokens once they are generated; it is up to the user to securely save this information. You cannot recover a token if it is lost. The scope of each token is securely encrypted directly into the token, which is decrypted by WEGnology server-side. This allows WEGnology to use the token to grant access to resources without having to store any information about the token directly. The benefit of this approach is that access tokens can never by obtained from any data stored on WEGnology’s servers.
Application Secret and Keys
Devices that communicate using MQTT use application secrets and keys. These are implemented in the same way as API Security Tokens, but automatically scope access to the specific application. The key and secret are used as MQTT’s username and password fields respectively.
Infrastructure Security
WEGnology uses Amazon AWS as its underlying infrastructure provider. Amazon complies with the strictest information and physical security requirements. Please refer to their security documentation for more information.
Two-Factor Authentication
WEGnology has implemented a Two-Factor Authentication (2FA) scheme based on the Internet Engineering Task Force standard RFC 6238. The same time-variant-based one-time password algorithm used by Google and Amazon also protects a WEGnology user’s account against unauthorized access even if their password has been compromised.
Was this page helpful?
Still looking for help? You can also search the WEGnology Forums or submit your question there.
