SAML: Verify Node
The SAML: Verify Node allows a workflow to verify and extract response data from a Security Assertion Markup Language 2.0 (SAML) single sign-on (SSO) identity provider.
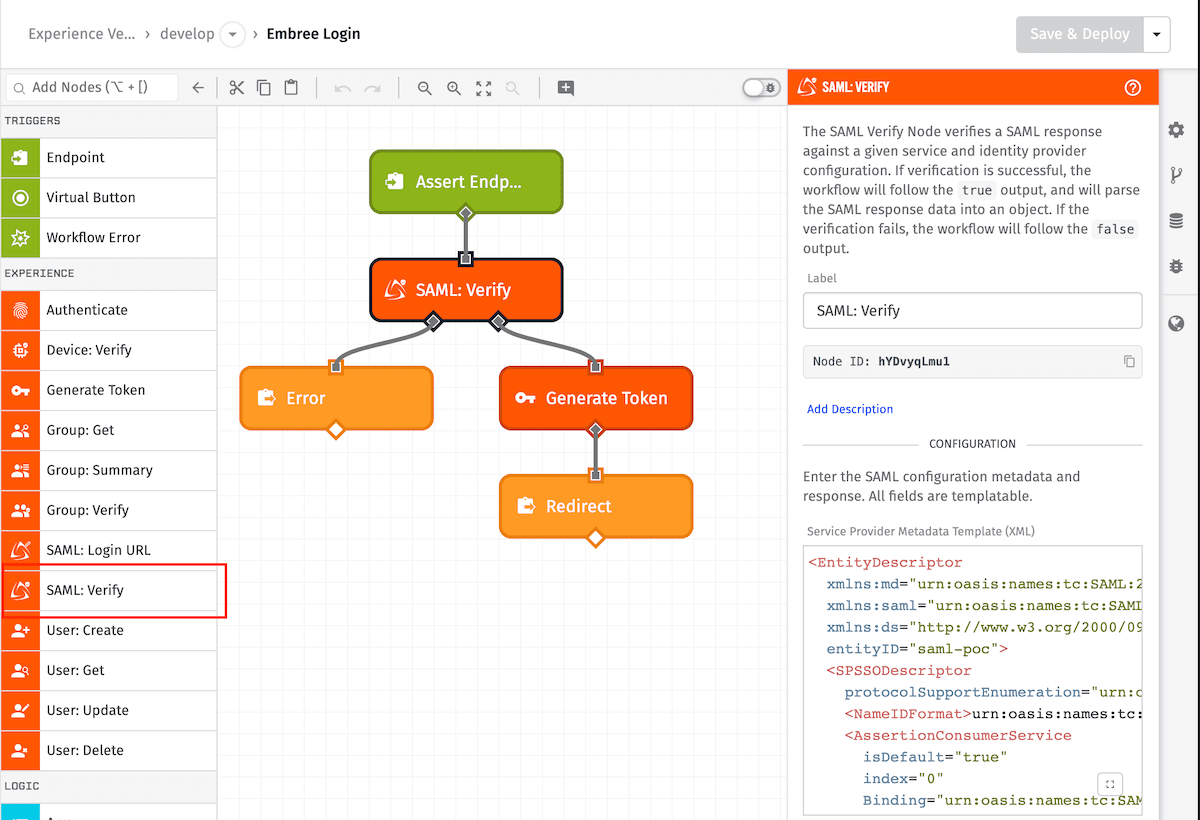
Node Properties
The configuration for the SAML: Verify Node requires two SAML 2.0 metadata XMLs and a SAML assertion response.
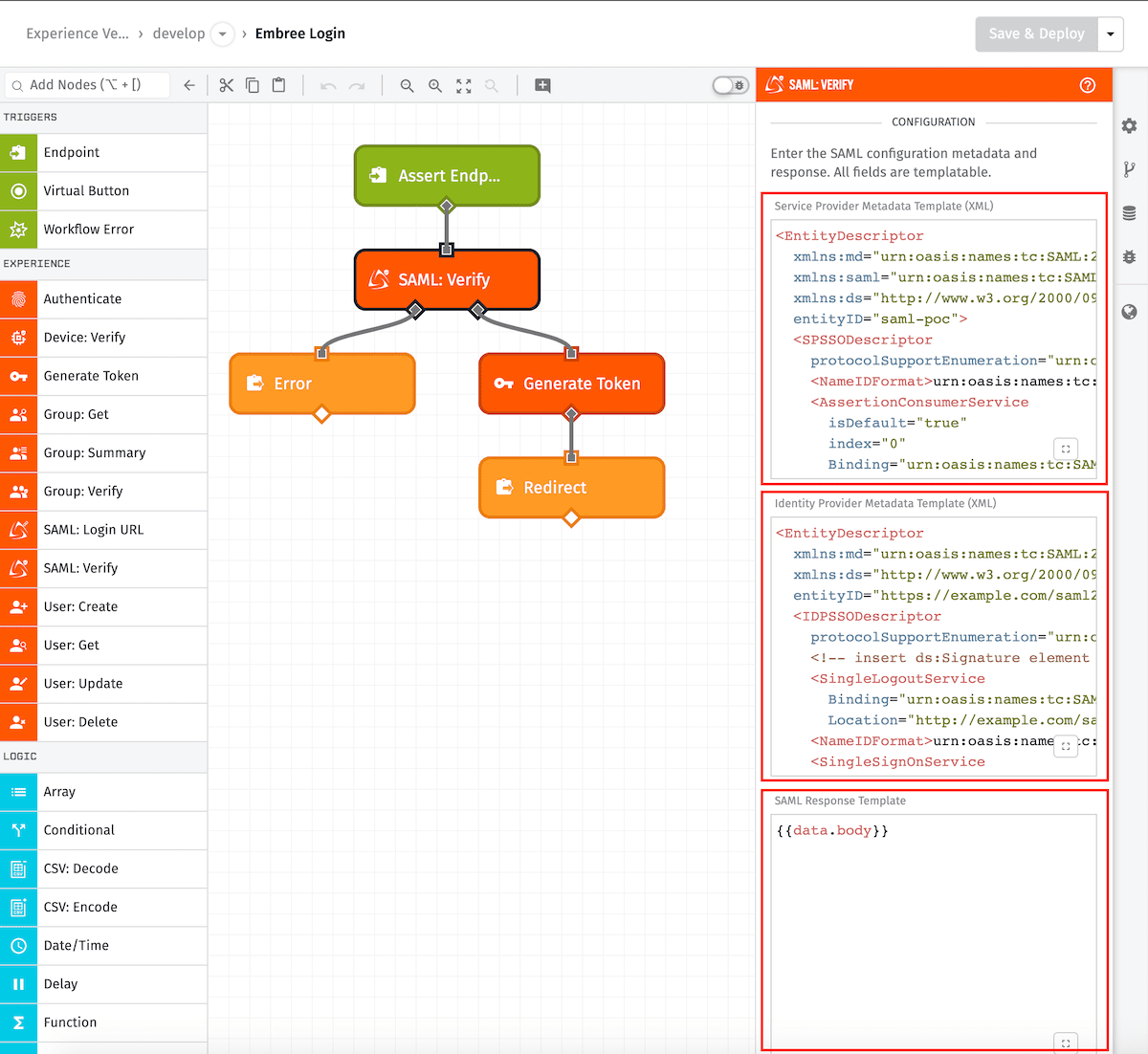
Configuration
Service Provider Metadata Template
An XML EntityDescriptor describing the service provider - this field supports templating. Here is an example:
<EntityDescriptor
xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata"
xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
xmlns:ds="http://www.w3.org/2000/09/xmldsig#"
entityID="saml-poc">
<SPSSODescriptor
protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<!-- optional ds:Signature element (omitted) -->
<NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</NameIDFormat>
<AssertionConsumerService
isDefault="true"
index="0"
Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Location="http://example.com:8090/saml/assert"/>
</SPSSODescriptor>
</EntityDescriptor>
Identity Provider Metadata Template
An XML EntityDescriptor describing the identity provider - this field supports templating. Here is an example:
<EntityDescriptor
xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata"
xmlns:ds="http://www.w3.org/2000/09/xmldsig#"
entityID="http://example.com/saml2/idp/metadata.php">
<IDPSSODescriptor
protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<!-- optional ds:Signature element (omitted) -->
<SingleLogoutService
Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect"
Location="http://example.com/saml2/idp/SingleLogoutService.php"/>
<NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</NameIDFormat>
<SingleSignOnService
Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect"
Location="{{saml.url}}"/>
</IDPSSODescriptor>
</EntityDescriptor>
SAML Response
A base64 encoded SAML 2.0 assertion from an identity provider. This field supports a static base64 encoded string or string templates.
Result Path
If the SAML response is verified, this is considered successful associated and the true (or right) path out of the node is taken. If the SAML response verification fails then the false (or left) path will be taken.
It is required you specify where on the payload path you want the extracted SAML assertion data to be placed. If the SAML verification is successful, it will store the extracted SAML data in an object at this path. If the validation errors, the result will be an object with an error property.
Node Example
Here’s an example output from running the above workflow ...
{
"working": {
"samlAssertion": {
"audience": "https://example.com/sso/metadata",
"attribute": {
"email": "user@esaml2.com",
"lastName": "Samuel",
"firstName": "E"
},
"conditions": {
"notbefore": "2015-10-26T11:41:43.500Z"
"notonorafter": "2015-10-26T11:46:43.500Z"
},
"issuer": ["https://sp.example.org/sso/metadata"],
"nameid": "user@esaml2.com",
"signature": "<Signature ... </Signature>",
"statuscode": {
"value": "urn:oasis:names:tc:SAML:2.0:status:Success"
}
},
...
},
...
}
Node Errors
The following is an example of a failed operation:
{
"working": {
"samlAssertion": {
"error": {
"message": "Multiple metadata entitydescriptor"
},
}
...
},
...
}
Related Nodes
Was this page helpful?
Still looking for help? You can also search the WEGnology Forums or submit your question there.